What Are SIM Swap Attacks & How Can You Protect Yourself?

In this article:
What Are SIM Swap Attacks & How Can You Protect Your Bitcoin Against Them?
For Bitcoiners, increased adoption of the digital currency has brought with it a growing threat. One of the most alarming ways hackers can exploit vulnerabilities is with a SIM swap attack. This allows malicious players to take control of your phone number and gain access to your most sensitive accounts, including those holding your BTC.
In this guide, we’ll break down what SIM swap attacks are, how they work, the signs to watch out for, and the steps you can take to protect your BTC holdings.
Key Takeaways
- SIM swap attacks are a form of identity theft that allows hackers to hijack your phone number by tricking your mobile provider and gaining access to your most sensitive accounts.
- SIM swap attacks enable unauthorized access by compromising your phone number and bypassing SMS-based two-factor authentication (2FA).
- Bitcoiners can protect themselves against SIM swap attacks by avoiding SMS-based two-factor authentication (2FA), using authenticator apps, and strengthening their account security.
What Are SIM Swap Attacks?
A SIM swap attack, also known as SIM swap fraud or SIM jacking, is a technique used by SIM scammers to gain access to and control of your phone number.
They do this by assuming the victim’s identity and deceiving your mobile provider into transferring the victim’s phone number to a SIM card that they control.
Once the transfer is done, the attacker can intercept all calls and text messages intended for the victim, including 2FA authentication codes, gaining complete control over the phone and any sensitive accounts, such as your BTC wallet.
SIM swap attacks are usually driven by financial motives, with criminals looking to access a victim’s bank accounts, Bitcoin wallets, and payment card information. However, in some instances, offenders may perform a SIM swap to extort the victim for control of their number, hijack social media accounts, or sell access to the victim’s phone number and linked accounts on the black market.
One of the most well-known SIM swap attacks targeted Jack Dorsey, the then-CEO of Twitter (now X), in 2019. Another high-profile incident occurred in 2024 when the U.S. Securities and Exchange Commission’s (SEC) X account was compromised in a SIM swap attack.
Understanding how these attacks work is crucial for staying protected.
“When we’re talking about keeping BTC safe, your phone number is almost as valuable as your private keys. SIM swap attacks exploit this gap, letting attackers steal 2FA codes and potentially drain custodial mobile wallets and exchange accounts. Protecting your bitcoin isn’t just about securing your seed phrase. It's about securing every possible entry point, especially the ones we tend to overlook,” explains Tony Yazbeck, co-founder of The Bitcoin Way.
How Do SIM Swap Attacks Work?
A subscriber identity module, commonly known as a SIM, is a small chip that enables calling, texting, and mobile data on your phone.
Each SIM card has a unique user identifier linked with just one mobile account. When this data is transferred to a new SIM card, the original stops working, and all calls, texts, and mobile data are rerouted to the replacement card. This is essentially how a SIM swap attack works.
Here’s a step-by-step breakdown of how a typical SIM swap attack unfolds:
- The attacker begins by collecting personal details about the owner of a phone number. This can be done through various methods, such as purchasing information on the black market, gathering data from the victim’s social media profiles, data breaches, phishing, or social engineering.
- The attacker then uses the collected information to contact the victim’s mobile carrier and convince them that they are the account owner.
- Once the identity has been “verified,” the attacker convinces the carrier to transfer the victim’s phone number to a SIM card they control by claiming they have lost the original SIM card.
- Once the SIM swap is complete, the criminal gains control of the phone number, receiving all calls and texts, including the victim’s 2FA codes that can be used to access bank accounts, crypto exchange accounts, and social media profiles.
- With access to a victim’s two-factor authentication, the cybercriminal can potentially access Bitcoin wallets, bank accounts, email accounts, and more.
Although less common, fraudsters can also carry out SIM hijacking by colluding with a mobile service provider employee and using a customer’s information to initiate a SIM swap attack.
Why Are SIM Swap Attacks a Danger for Bitcoiners?
Bitcoin holders face unique security challenges because many (custodial) Bitcoin wallets and exchanges rely on SMS-based 2FA for security. SIM hijackings are especially dangerous for Bitcoiners because they can result in the complete theft of their assets.
Once an attacker successfully executes a SIM swap, they can bypass security measures and intercept a victim’s 2FA codes, reset passwords/PINs, and gain unauthorized access to any holdings.
Given the decentralized nature of BTC, it becomes nearly impossible to recover funds. This makes BTC holders high-value targets for SIM swap attacks; one of the many reasons bitcoin privacy is so important.
Securing your bitcoin and protecting it from threats such as SIM swap attacks can feel complex. However, you don’t have to do it alone. A trusted Bitcoin consultancy can help provide expert guidance and tailored solutions to help protect your BTC.
How to Prevent SIM Swap Attacks: Step-by-Step Guide
Fortunately, there are multiple cybersecurity practices that can help you reduce the risk of falling victim to SIM swap attacks. Here’s how you can protect your BTC:
- Avoid using SMS-based two-factor authentication methods and switch to authenticator apps or hardware security keys.
- Store your BTC in air-gapped Bitcoin wallets offline.
- Limit your personal information exposure by being cautious about what you share online.
- Regularly monitor your mobile account activities for any unauthorized activities by setting up alerts with your carrier, if available.
- Use an encrypted, secure email and avoid linking email recovery options to your phone number.
- Contact your telecommunications provider to activate enhanced account security protocols.
- For Bitcoiners, consult a Bitcoin consultancy to audit your SIM setup and provide guidance on best practices.
Taking these steps can significantly reduce your risk of falling victim to a SIM swap attack.
What Are the Signs of a SIM Swap Attack?
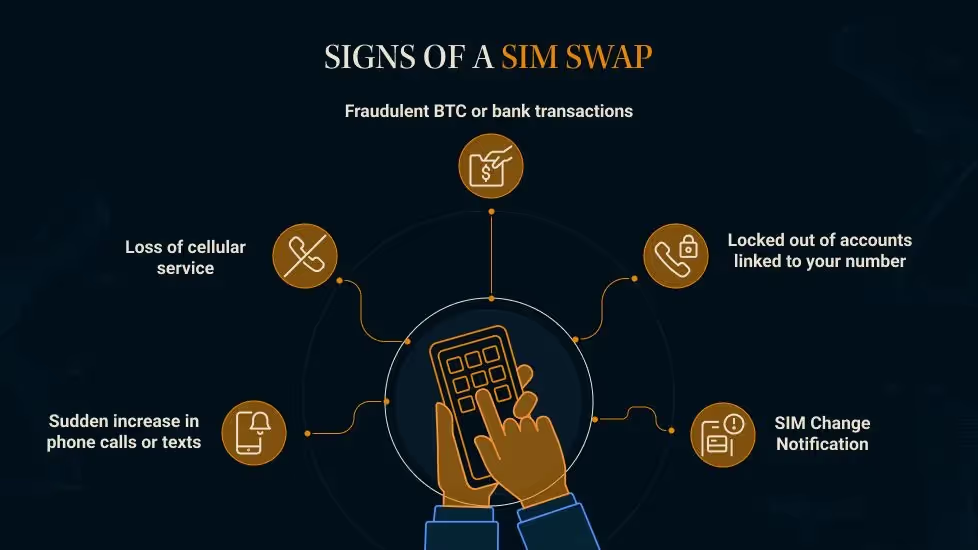
The signs of a SIM swap attack are often easy to identify and tend to become obvious after the attack. Below are some common signs of a SIM swap attack.
- Fraudulent BTC or bank transactions: Unauthorized transactions or withdrawal attempts from your BTC wallet or financial accounts.
- Locked out of accounts linked to your number: If you are suddenly unable to log in to your key accounts, such as bank accounts, emails, or exchanges.
- Loss of cellular service on your phone: Your phone unexpectedly loses signal, making it impossible for you to receive calls or texts to your phone number while other users around you remain unaffected.
- Mobile carrier notifies you of SIM number changes: You receive a message from your mobile service provider about a SIM card change request you did not initiate.
- Sudden increase in phone calls or texts: You receive a surge of phone calls or texts from an unknown number. This can be carried out as a distraction technique used by cybercriminals during a SIM swap attempt.
What to Do if You Become a Victim of a SIM Swap Attack
If you suspect your SIM card has been compromised, taking prompt action is crucial to minimizing the damage.
Here’s what to do if you become a victim of a SIM swap attack:
- Contact your mobile service provider immediately and report the unauthorized SIM swap. Ask them to freeze your account and restore service to your original SIM card.
- Contact your financial institution and/or Bitcoin exchange and notify them of the SIM swap, requesting that they temporarily freeze your account and any unauthorized transactions or withdrawals.
- Review all your major accounts and update your passwords to keep them secure. If you're using SMS-based 2FA, switch to an authenticator app immediately.
- File a police report, as it can help with recovery efforts and insurance claims, if applicable.
- Closely monitor your account over the next few days for any unusual activities and set up alerts where possible.
With a SIM swap attack, time is of the essence. It is imperative that you act quickly to limit damage.
Learn How to Protect Your BTC With The Bitcoin Way
If you want to learn how to protect your BTC, it’s best to consult professionals who have specialist, relevant expertise. This can help you avoid costly mistakes.
The Bitcoin Way can offer you personalized guidance on how to protect and secure your BTC holdings from SIM swaps and other attacks.
FAQs
Can a SIM swap attack happen if I use a hardware wallet?
A SIM swap attack can’t directly compromise your hardware wallet because the private keys that control your BTC are stored offline. However, it can still pose a threat, especially if you rely on SMS-based two-factor authentication as part of your wallet management.
What should I tell my mobile provider to reduce SIM swap risk?
To reduce the risk of a SIM hijacking, you can request stronger account protection. This can include setting up a passcode or PIN that must be provided before any changes can be made to your SIM card. You can also ask your provider to require government-issued ID or in-person verification before approving any SIM swap or account changes.
How fast can a SIM swap attack happen?
SIM swap attacks can happen in a matter of minutes once an attacker has gathered enough personal information about a victim. They can then use social engineering or stolen data to trick a mobile service provider into transferring your phone number to a SIM card they control, effectively hijacking your number almost instantly. The entire process depends on how quickly the attacker can convince the mobile carrier to make the swap.
Is two-factor authentication safe from SIM swap attacks?
SMS-based two-factor authentication (2FA) is not safe from SIM swap attacks. If a cybercriminal successfully swaps your phone number, they can intercept 2FA codes required to access your accounts. However, app-based two-factor authentication apps can be safe from SIM swap attacks as they are not linked to your phone number and can’t be compromised via a SIM swap.
